Solutions & services
10hacken is offering consultancy services in cybersecurity, digital risk, compliancy & governance.
As a service provider of the Vanta platform we support our clients with the best solutions to reach compliance. Vanta's trust management platform takes the manual work out of your security and compliance process and replaces it with continuous automation—whether you’re pursuing your first framework or managing a complex program.
5-step guide for updating your security processes
As part of our consultancy services we can walk you through the five steps you should follow to update your security processes
Step 1: take inventory of your security tasks
The first step is to understand the current state of your security program. In this stage, you want to create a complete picture of your current tasks, processes, and workflows. Start by identifying all of the tasks on your plate. What tasks are you responsible for completing over a typical week, month, and year?
Step 2: identify which processes need updating
Now you’ll assess each of your processes and prioritize them. This step will help you identify which ones to transform and decide which to update first based on their potential impact. This impact will be determined by time saved, potential risk, and reduced cross-functional complexity.
Step 3: Make the needed changes
Now that you’ve identified which of your security processes to update, it’s time to take action and improve them. Looking at the high-impact tasks you’ve identified, consider how you can centralize them, integrate them into existing workflows, and automate them.
You’ll likely need a trust management platform to help you centralize, integrate, and automate your security program. If you do not already have a platform to help you manage your security, find a platform that streamlines the process and workflows you identified as most impactful.
Step 4: Influence your team to change
Next, align with your cross-functional stakeholders and co-create workflows with them. Your goal is to find a solution that’s mutually beneficial and creates a better working model for both teams, enabling them to execute in their existing workflows and systems while moving projects forward.
Tailor your approach to the team you’re collaborating with and the tasks you need to accomplish with them.
It’s also important to share how this new process will benefit them. Some examples include preventing them from veering from their day-to-day processes, reducing last-minute requests, and more automation and alerts for deadlines, etc
Step 5: adapt as your organization grows
The final step is to monitor your processes, integrations, and automations over time to ensure they’re scaling with yourbusiness. This step will be ongoing and done on a regular cadence. Establish a reporting procedure and cadence that monitors the impact and value of your security program. Communicate the insights across your leadership and cross-functional teams. Monitor and improve the overall operations of your program and scale your processes as your organization grows.

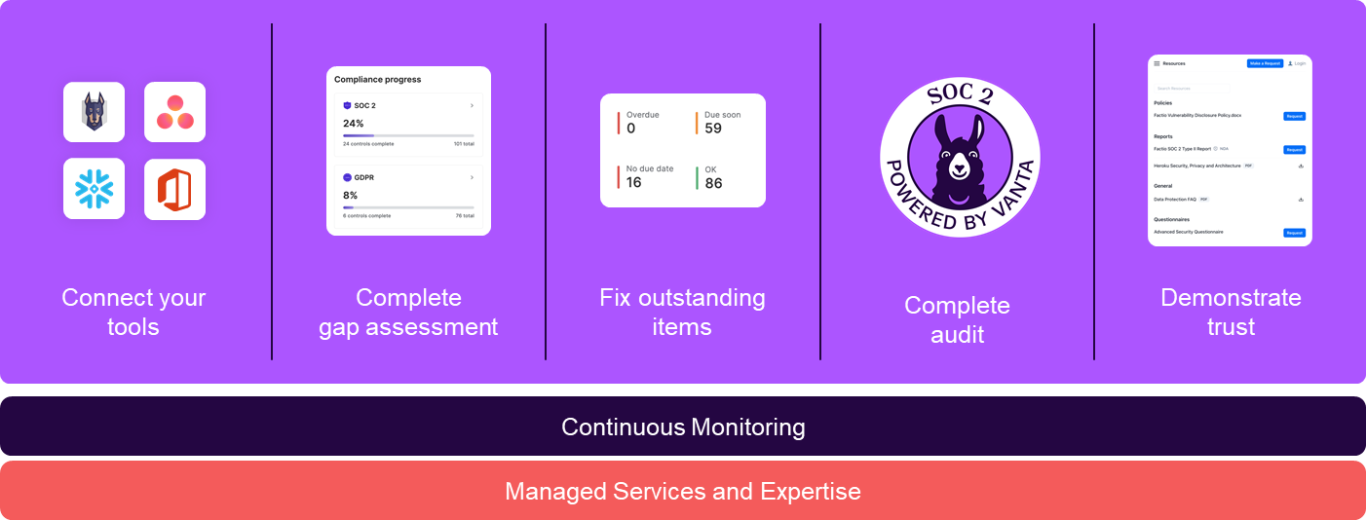
10hacken partners with Vanta to support organisations on their ISO 27001 journey. With a streamlined process and timeline (example in picture) we help our clients to be ready for the ISO 27001 audit
ISO27001

In a couple of easy steps your organisation is ready to demonstrate trust!
©Auteursrecht. Alle rechten voorbehouden.
We hebben je toestemming nodig om de vertalingen te laden
Om de inhoud van de website te vertalen gebruiken we een externe dienstverlener, die mogelijk gegevens over je activiteiten verzamelt. Lees het privacybeleid van de dienst en accepteer dit, om de vertalingen te bekijken.
